Are Your Executives Sitting Ducks? 7 Dark Web Threats Standard Security Can't Detect
- Corbin Emmanuel
- Oct 29, 2025
- 6 min read
Updated: Oct 30, 2025
Your executives are walking around with targets on their backs, and your standard security tools are basically blind to the biggest threats they face. While your firewall is busy blocking port scans and your antivirus is updating signatures, cybercriminals are trading your CEO's personal information, planning sophisticated attacks, and building detailed profiles of your leadership team: all in the shadowy corners of the internet where traditional security can't see.
The dark web has become the ultimate hunting ground for executive-focused attacks, and the statistics are sobering. Recent studies show that 72% of executives have been personally targeted by cybercriminals, with these attacks increasing at companies that have already been hit once. Your executives aren't just high-value targets: they're sitting ducks in an ecosystem designed for predators.

1. Credential Stuffing and Account Takeovers
Here's the thing about executives: they're human. They reuse passwords, they sign up for services, and their credentials end up in data breaches just like everyone else's. But when an executive's login gets compromised, the impact is catastrophic.
Cybercriminals don't just try these stolen credentials on random sites: they specifically target executive email accounts, cloud services, and business applications. Once they're in, they can monitor communications, steal sensitive business information, or launch business email compromise attacks that can cost companies millions.
Traditional security systems see these logins as legitimate because, technically, they are. The credentials are real, the access patterns might look normal, and by the time anyone notices something's wrong, the damage is done.
2. Executive Doxing and Personal Information Sales
The dark web marketplace for executive personal information is thriving. Cybercriminals compile comprehensive "fullz" packages containing everything from home addresses and family details to financial records and travel patterns. This isn't random data: it's carefully curated intelligence designed to enable targeted attacks.
These packages often include details that most executives don't realize are public: property records, business registrations, social media check-ins, and even information from loyalty programs. Criminals use this data to craft incredibly convincing spear-phishing attacks, plan physical surveillance, or simply sell it to the highest bidder.
Your network security tools have zero visibility into these marketplaces where your executives are being discussed, analyzed, and targeted.

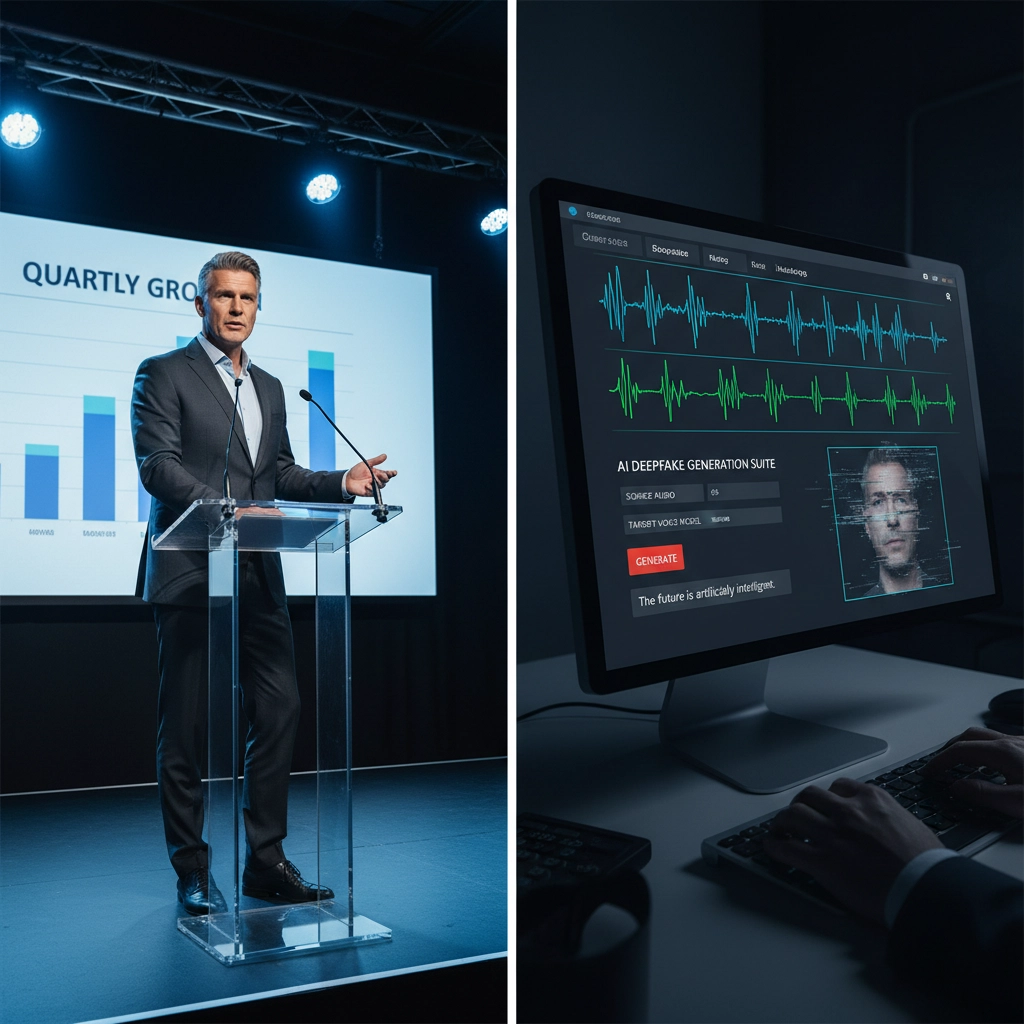
3. Deepfake Voice and Video Creation
With just a few minutes of audio from earnings calls, conference presentations, or public interviews, cybercriminals can create convincing deepfake audio of your executives. These aren't the clunky, obviously fake attempts you might imagine: modern AI tools can produce audio that fools even people who work closely with the targeted executive.
These deepfakes are used for business email compromise attacks, fraudulent wire transfers, and social engineering campaigns targeting other executives or key employees. The criminals will call your CFO pretending to be your CEO, complete with a voice that sounds exactly right, requesting an urgent transfer to a "new vendor."
Traditional security focuses on email security and network monitoring, but it can't detect when someone three time zones away is training an AI model on your CEO's voice.
4. Insider Trading Intelligence and Corporate Espionage
The dark web hosts active marketplaces for corporate intelligence that could impact stock prices. Disgruntled employees, hackers who've gained network access, and even sophisticated nation-state actors sell everything from merger plans to earnings information before it becomes public.
This information doesn't just damage your company: it creates a feedback loop that makes your executives even bigger targets. When criminals know your company is planning a major acquisition or facing significant challenges, they can time their attacks for maximum impact and leverage.
Your security team might eventually detect the data exfiltration, but by then the information has already been sold, shared, and potentially acted upon by bad actors.
5. Swatting and Physical Threat Coordination
One of the most dangerous trends in executive targeting is the coordination of physical threats through dark web forums. "Swatting": making false emergency calls to send armed law enforcement to an executive's home: has moved from online gaming disputes to serious executive targeting.
Cybercriminals share intelligence about executive home addresses, family schedules, and security measures. They coordinate harassment campaigns, plan surveillance operations, and even discuss more serious physical threats. These aren't just keyboard warriors: some of these threats translate into real-world danger.
Traditional cybersecurity doesn't monitor for discussions about your executives on criminal forums, and by the time a physical threat manifests, it's too late for digital defenses.
6. Executive Impersonation and Brand Damage
Cybercriminals create fake social media profiles, email accounts, and even business registrations using your executives' names and likenesses. These impersonation attempts aren't always about immediate financial fraud: sometimes they're about long-term reputation damage or preparing the groundwork for future attacks.
A fake LinkedIn profile of your CEO might be used to connect with employees, gathering intelligence about internal operations. Fake email accounts might be used to register for services or make statements that damage your company's reputation. These attacks often fly under the radar for months before anyone notices.
Your security tools monitor your official accounts and domains, but they can't track every platform where someone might be impersonating your leadership team.
7. Supply Chain and Partner Targeting
Here's where it gets really insidious: cybercriminals don't just target your executives directly: they target the people and organizations your executives interact with. Vendors, business partners, family members, and personal service providers all become potential attack vectors.
A criminal might compromise your CEO's personal accountant to gain access to financial information, or they might target a key vendor to establish a foothold for future attacks against your company. These indirect approaches are incredibly difficult to detect because the initial compromise happens entirely outside your security perimeter.
Traditional security assumes the threat comes from outside trying to get in, but these attacks are already inside your extended business ecosystem before they ever touch your network.
Why Standard Security Systems Miss These Threats
The fundamental problem with traditional cybersecurity is that it's designed to protect networks, not people. Your firewalls, endpoint protection, and SIEM systems are incredibly good at detecting known malware, blocking unauthorized network access, and alerting on suspicious file activity.
But executive-focused attacks don't start with malware. They start with intelligence gathering, social engineering, and human manipulation. By the time these attacks touch your network infrastructure, they've already succeeded.
Standard security also operates on the assumption that you can draw a clear line between "inside" and "outside" your organization. But executives don't live their entire lives within your corporate network. They use personal devices, access public Wi-Fi, and maintain relationships and accounts that extend far beyond your security boundary.

The Human-Led Alternative
This is exactly why Engaged Security Partners takes a fundamentally different approach to executive protection. Instead of waiting for threats to hit your network, our human analysts actively monitor the spaces where these threats originate.
Our threat intelligence team maintains visibility into dark web marketplaces, criminal forums, and underground networks where executive targeting actually happens. We don't just rely on automated tools that might miss context or nuance: we have experienced analysts who understand how these criminal ecosystems operate and can identify threats that would never show up in traditional security logs.
When we detect your executives being discussed, their information being sold, or threats being planned against your organization, we don't wait for the attack to materialize. We provide immediate intelligence and work with you to implement preventative measures that address the threat at its source.
This human-led approach means we can catch threats that automated systems would never see: the subtle planning discussions, the intelligence gathering phases, and the relationship building that precedes sophisticated attacks.
Taking Action Before It's Too Late
Executive targeting isn't going away: it's getting more sophisticated, more organized, and more dangerous. The criminals who operate in these spaces are professional, well-funded, and incredibly patient. They're playing a long game that your traditional security tools simply aren't designed to counter.
The question isn't whether your executives will be targeted: it's whether you'll know about it in time to do something about it. In a threat landscape where attacks often begin months before they touch your network, visibility into the planning phases isn't just helpful: it's essential.
Your executives don't have to be sitting ducks. But protecting them requires a security approach that goes beyond your network perimeter and into the spaces where these threats actually originate. It requires human intelligence, not just artificial intelligence. And it requires action before the attack, not just reaction after the damage is done.

Comments